Windows Autopilot
How It Works & How to Set It Up
These are the best practices and tips to set yourself up for success with Windows Autopilot. Windows Autopilot is a feature within Intune that allows you to send devices directly from hardware providers to end users.

New device provisioning is foundational to cloud attach and cloud-based update management. During initial Windows setup, Autopilot enables users to enroll their device through Intune device management, so PCs get to a managed and productive state without reimaging.
Principal GPM for Microsoft Windows, Jason Githens, compares the benefits and tradeoffs of Azure AD Join versus Windows Autopilot and shows how to enable Windows Autopilot for easy device enrollment.
No pre-prep. Direct delivery to end users.
Get automatic policy and app implementation. Compare the benefits and tradeoffs of Azure AD join vs. Windows Autopilot.
Configure profile and security baselines that scope to all devices.

Take a look at admin options and setup for Windows Autopilot.
Set up enrollment to be co-managed when installing dozens of apps for new device provisioning.

See more pro-tips and what’s behind Windows Autopilot.
Watch our video here.
QUICK LINKS:
00:00 — Introduction
00:39 — Options to enroll devices into Intune
02:56 — Benefits and tradeoffs of Windows Autopilot
04:05 — Admin setup
05:07 — Autopilot settings
07:37 — Tips for success
08:43 — Wrap up
Link References:
Get started at https://aka.ms/WindowsAutopilotDocs
Check out our playlist for Windows cloud-based management at https://aka.ms/ManagementMechanics
Unfamiliar with Microsoft Mechanics?
As Microsoft’s official video series for IT, you can watch and share valuable content and demos of current and upcoming tech from the people who build it at Microsoft.
- Subscribe to our YouTube: https://www.youtube.com/c/MicrosoftMechanicsSeries?sub_confirmation=1
- Talk with other IT Pros, join us on the Microsoft Tech Community: https://techcommunity.microsoft.com/t5/microsoft-mechanics-blog/bg-p/MicrosoftMechanicsBlog
- Watch or listen from anywhere, subscribe to our podcast: https://microsoftmechanics.libsyn.com/website
- To get the newest tech for IT in your inbox, subscribe to our newsletter: https://www.getrevue.co/profile/msftmechanics
Keep getting this insider knowledge, join us on social:
- Follow us on Twitter: https://twitter.com/MSFTMechanics
- Share knowledge on LinkedIn: https://www.linkedin.com/company/microsoft-mechanics/
- Enjoy us on Instagram: https://www.instagram.com/microsoftmechanics/
- Loosen up with us on TikTok: https://www.tiktok.com/@msftmechanics
Video Transcript:
-Coming up, we’ll go inside Windows Autopilot with the mechanics of how the service works, best practices for configuring it, as well as a few tips to set yourself up for success. Continuing on in our series on cloud-based Windows management, where we’ve demonstrated the importance of cloud attach and cloud-based update management, new device provisioning is foundational to the experience. And Windows Autopilot is a feature in Intune that allows you to send new devices directly from your hardware providers to end users. Then, during initial Windows setup, Autopilot enables the user to enroll their device into Intune device management, so that the PC gets to a managed and productive state without needing to reimage it.
-Windows Autopilot is actually one of four primary options to enroll Windows device into Intune. I’ll start with the options using a device that has already been set up and is running Windows 10 or Windows 11. Here, users can self-enroll their personally own devices by installing the Company Portal app, then register the device using a Microsoft 365 work or school account. If you have set up auto enrollment in Azure AD and Intune, the user will only need to enter their credentials once.
-The second option that you’re probably familiar with is Workplace Join. Enrolling from Windows settings and the access work or school menu, then choosing connect and signing in with your org account. Both of these options are intended for personally owned devices. The option from the Windows settings is called MDM only enrollment and isn’t recommended. That’s because it does not register the device with Azure Active Directory and can prevent access to things like your organization’s email or security capabilities like conditional access. So those are the options for enrolling a running PC, but for a new corporate owned PC, you have a few additional options.
-First, you can sign into Windows using the same Microsoft 365 work or school account during Windows setup. This is called Azure Active Directory Join. And again, if auto enrollment is enabled for your Azure AD and Intune environment, the device will get automatically enrolled in one step. Then, Windows Autopilot is another option where the user is offered the option to sign into their work or school account with a streamlined experience for the user during setup. With these two options during Windows setup, devices will be marked as corporate-owned devices in Intune. And using any of these four options after the device is enrolled with Intune, and based on what you’ve set up as required configurations, Intune will install your apps and apply policies required to connect your organization’s data and services.
-The advantage of the first user self-enrollment and Azure AD join options are primarily with flexibility, in that any Windows 10 or Windows 11 Pro or Enterprise device can use this approach without any pre-prep or coordination with your hardware providers. And as long as your users are aware of Intune enrollment options and procedures, those devices can also be directly delivered from hardware providers to end users. And after device enrollment, devices will have your required policies and apps applied automatically. This option works well for unregistered devices, also referred to as commercial OOBE.
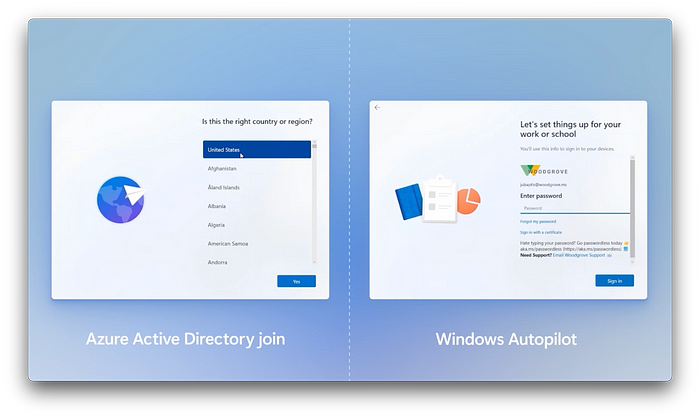
-Windows Autopilot on the other hand is used when you want to register devices to your tenant and establish organizational ownership of devices in advance. Now let’s go deeper on the benefits of Autopilot compared to the other options. To display a few benefits versus Azure AD join, I’ll walk through the screens for Windows 11 setup with and without Autopilot enabled. On the left, we’re using Azure AD join and on the right we’re using Autopilot. As we go through the experience, you’ll see that with Autopilot, the big advantage for the user is in its streamlined setup, removing the keyboard config screens, Microsoft license terms, and after the enrollment status page, the privacy setting screen is also taken care of. Then importantly, Autopilot can also enforce that the user account setting up the device is set up to be a standard user account for security reasons, not a local device administrator.
-Another capability worth noting that applies to both Azure AD join and Autopilot methods that you just saw, is the enrollment status page, which is a screen that displays installation progress to the user during setup. And as an admin, you can optionally block device usage until all apps and profiles are installed, ensuring the device is fully business-ready before a user can interact with it.
-So now that I’ve shown the options for device enrollment and the Windows Autopilot experience versus Azure AD join, let’s switch gears to the admin options for setting up your Intune environment, so that any Intune enrolled device receives your required apps and policies, then I’ll show you how to set up Windows Autopilot. First, you can use configuration profiles to configure all of your required policy settings, as well as default Wi-Fi settings and more. You’ll see that I have several created here, and many of these are targeted to all devices. To save time, in endpoint security, security baselines, you can easily create policies with Microsoft security recommendations enabled by default, that you can scope to all devices. Here, you can see all of the categories. I’ll expand this one for application management, and you’ll see a few important settings to block unwanted app installation. Finally, if I navigate to my Windows apps, these ones marked all are installed on all enrolled devices, and the ones without the all prefix are optional apps that users can self-install.
-Again, regardless of how a device enrolls into Intune management, it will automatically get the settings applied for my configuration profiles and security baseline, as well as the apps I just showed their defaults for all devices. Now with my foundational configuration set, let’s move on to Windows Autopilot settings. I’ve navigated to device enrollment, under Windows Autopilot deployment program, you’ll see the deployment profiles as well as devices. Now to give you an idea of how the devices and deployment profiles apply in this scenario, here’s how the Autopilot workflow works. Windows Autopilot works by using unique hardware IDs that get assigned to your organization.
-When a device with a hardware ID that you own connects to the internet and the Autopilot service during setup, it applies a set of policies that you’ll configure using an Autopilot deployment profile that I’ll show in a minute. Then after the user signs in, it’s just the standard Intune device enrollment with the option to display the enrollment status page, or go straight to an active desktop. Let me show you how this works. In my case, my hardware provider registered hardware details for each machine on my behalf. And in the admin center, I can optionally assign a user to a device so that once they connect to the internet, it will automatically show their username for initial sign-in like we saw before. And by the way, you have the option to block unregistered devices, so that only devices you trust can enroll.
-Now, the Autopilot service knows that those devices belong to my organization, so I just need to provide the service a few instructions so it can streamline the setup experience. To do that, I’ll create the deployment profile, give it a name, Mechanics, I’ll select the mode, the most common mode is user-driven, in my case, I’ll stick with that. I’ll also keep Azure AD joined, but hybrid Azure AD joined is another option. For the rest, I’ll keep the defaults to skip licensing, privacy, and keyboard configuration screens. And before I move on, this option here for pre-provision deployment allows IT to take initial delivery of the device to set it up with apps and policies, then forward it onto its user.
-Next, in assignments, I can add the groups I want to scope for this profile, and now I just need to review and create the profile. To complete the experience, I’ll show you how to set up the enrollment status page. This configuration isn’t in the Autopilot section for device enrollment, because it applies to both Azure AD join and Autopilot as I mentioned earlier. I’ll go ahead and create a new instance, name it Mechanics. This is where you enable it, so I’ll set the show app and profile configuration progress to yes, and here I can define a timeout period and whether to show a custom message. Below that is where I can block device usage if I want until provisioning is complete. And I’ll keep the rest of the defaults. Now I just need to assign, add optional tags, and review, that’s it, and I have everything set up for my hardware partner to start delivering devices to my user.
-Next, with everything running, let me give you a few tips that will help ensure success with your Autopilot Azure AD join or self-enroll based deployments. First, if you’re currently using tools like task sequences and Configuration Manager for image based deployment or app sequences, Windows Autopilot should not be thought of as a direct replacement to that. And even if you’re amazing at scripting complex multi-app installs, it won’t be as reliable as a task sequence. If you need to install dozens of apps for a new device provisioning, you’ll probably want to set up Azure AD join or Autopilot device enrollment to be co-managed. Then let Configuration Manager take over once the device is under management, so it can run an app only task sequence.
-Another option to look into is just installing a small core set of apps like Office, a VPN client, and a few other must-have apps. If you recall, those are the ones I had marked as all before in my apps list. Then, let the users self-select additional apps they might need using the company portal, like the ones we saw before without the all naming prefix. If users are okay installing apps with Google Play or on Android or the App Store on iOS, there are probably happy to self-select a few apps they need from the company portal and Windows too.
-So now, you know how Windows Autopilot works and how it compares with other enrollment and provisioning options using Intune. To learn more, check out aka.ms/WindowsAutopilotDocs. Check out our complete list for Windows cloud-based management at aka.ms/ManagementMechanics. And keep checking back to Microsoft Mechanics for all the latest tech updates. Subscribe if you haven’t already, and thanks for watching.
